Als onderdeel van het Quantum Delta NL programma is een consortium van Havenbedrijf Rotterdam, Q*Bird, Single Quantum, Cisco, Eurofiber, Portbase, Intermax en InnovationQuarter erin geslaagd om als eerste ter wereld een schaalbare quantum netwerkverbinding aan te leggen in de haven van Rotterdam. In een proefopstelling is aangetoond dat door het gebruik van quantum technologie de toegang tot gevoelige informatie onmogelijk wordt gemaakt. Dit nieuwe communicatiesysteem kan in de toekomst de veiligheid van de tienduizenden zeeschepen die de haven jaarlijks bezoeken verbeteren en ook het economische verkeer dat daaruit voortvloeit beter beveiligen tegen de dreiging van quantum computers.
Bron: InnovationQuarter
Distributie quantum sleutels
Tijdens de proefperiode, die eind 2022 is gestart, is er door Q*Bird in het datacentrum van Eurofiber een centrale hub voor het creëren van een quantum netwerk geïnstalleerd. Deze centrale hub is verbonden met twee eindpunten bij Portbase en Havenbedrijf Rotterdam. Deze twee eindpunten hebben tijdens de proefperiode data uitgewisseld die beveiligd is met quantum sleutels. Het genereren en verdelen van de sleutels, vindt plaats binnen het quantum netwerk, waarbij Q*Bird een unieke multipoint-to-multipoint configuratie voor de eindpunten gebruikt. Aan de centrale hub kunnen vele nieuwe eindpunten worden gekoppeld die elk quantum sleutels kunnen genereren.
Andere quantum sleutel-distributiesystemen berusten op een minder flexibele peer-to-peer-configuratie. Q*Bird is de enige ter wereld die dit schaalbare systeem aanbiedt. Het systeem kan ook gebruikt worden voor de beveiliging van andere kritieke infrastructuur netwerken in Nederland. Nu deze proef geslaagd is, zullen in de loop van dit jaar nieuwe eindpunten bij de Douane en een aantal nautische dienstverleners in de haven worden aangesloten op de centrale hub.
Klaar voor de toekomst
De opzet die tijdens de proef is gebouwd maakt het in de toekomst mogelijk om meerdere eindgebruikers van een veilige, niet af te tappen verbinding te voorzien. De kracht van deze opzet is het gemak waarmee deze kan worden uitgebreid tot veel meer gebruikers en de relatief lage kosten van uitbreiding. Na aansluiting kunnen betrokken partijen er zeker van zijn dat er niet is geknoeid met de communicatielijn. Als een hacker probeert de sleutels te stelen, dan zorgen de wetten van de quantum mechanica ervoor dat de gebruikers worden geïnformeerd zodra de sleutels gecompromitteerd zijn. Een andere set sleutels wordt dan aangemaakt om verdere berichten veilig te kunnen uitwisselen.
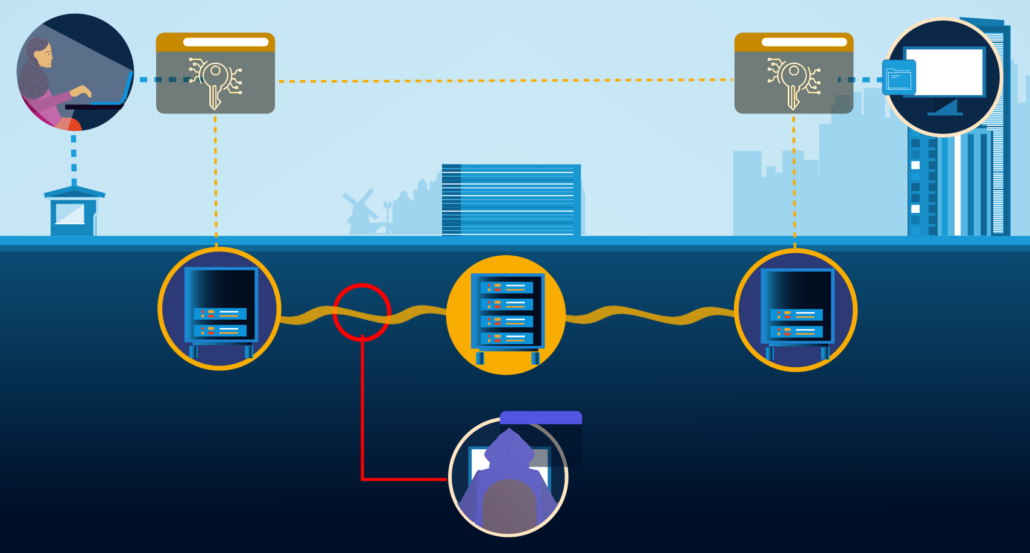
Schematische afbeelding van het quantumsleutel-distributiesysteem. Een centraal knooppunt (Charlie) verbindt gebruikers Alice (links) en Bob (rechts). Als een afluisterende hacker probeert de geheime sleutels te stelen, zorgen de wetten van de quantummechanica ervoor dat de gebruikers worden geïnformeerd als de sleutels gecompromitteerd zijn. Een andere set sleutels wordt dan aangemaakt om verdere berichten veilig te versleutelen.





